Increasingly sophisticated threats. Expanding attack surfaces. A lower barrier to entry for attackers. It's tough out there for security teams. All of these factors and more create persistent risk for even the most technically sophisticated organizations. Point-in-time and reactive approaches to cybersecurity are no longer sufficient to stave off adversaries.
With that in mind, many security leaders are prioritizing adopting a continuous threat exposure management (CTEM) framework as part of their security strategy.
What is continuous threat exposure management (CTEM)?
CTEM is a structured, proactive framework that enables organizations to identify, prioritize, and mitigate risk over time to maintain a healthy security posture and hygiene. By providing a holistic and continuous profile of your system’s exploitable vulnerabilities, misconfigurations, and weaknesses, teams can more efficiently prioritize technical and strategic efforts.
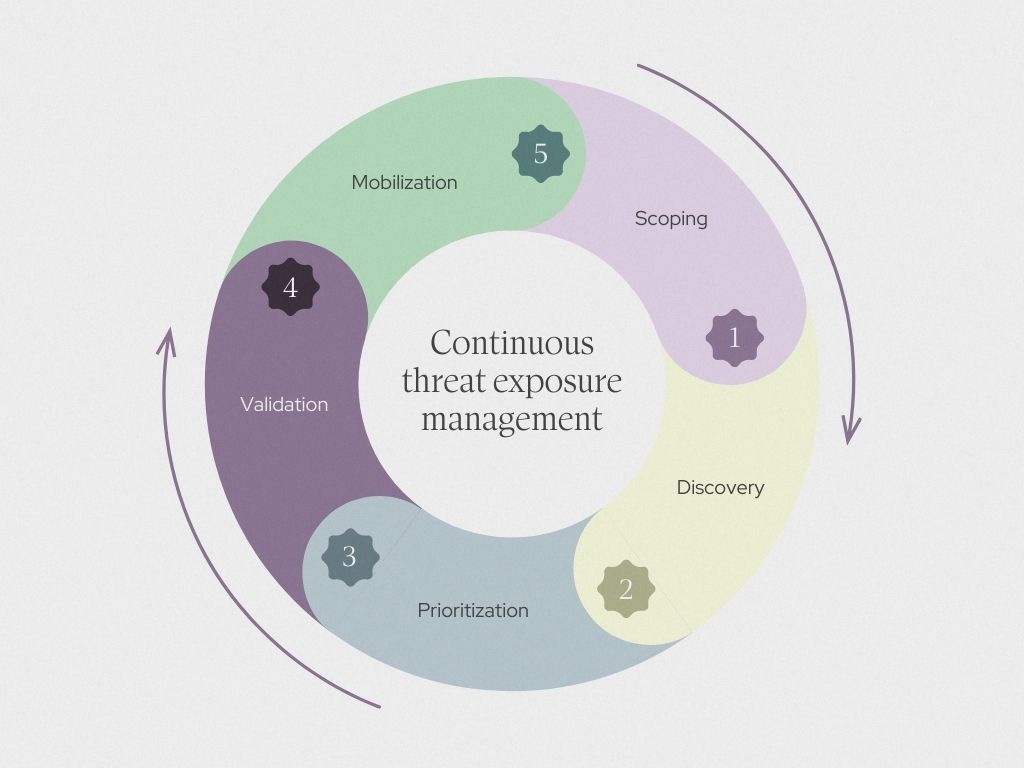
While many leaders are afforded the budget to undertake a CTEM project, actually implementing it can require significant resources across new people, processes, and platforms. Gartner defines 5 stages of any CTEM initiative, which we'll break down to put your team in a position to effectively deploy at your organization:
- Scope: Define the objectives, boundaries, and desired outcomes of your program while identifying key stakeholders and assets to prioritize.
- Discover: Identify and assess existing security vulnerabilities and risks while mapping out your current threat landscape.
- Prioritize: Focus efforts on addressing the most critical vulnerabilities and threats, enabling teams to allocate resources effectively and reduce risk impact.
- Validate: Confirm the effectiveness of implemented security measures through testing and analysis, ensuring alignment with organizational goals and compliance standards.
- Mobilize: Develop and execute a clear, actionable security strategy, empowering teams to implement solutions and respond effectively to emerging threats.
Scope and understand your attack surface
The first step in any CTEM program is building a comprehensive understanding of your existing environment. This should include a detailed picture of the attack surface including infrastructure, assets, and whatever security controls are being leveraged to establish your defensive posture. Without a precise scope, your efforts to detect and mitigate threats could be undermined.
To ensure an efficient and manageable start, narrowing the scope of your program for an initial pilot might be beneficial. In this case, focusing on a specific segment of your attack surface, such as SaaS applications in a work-from-anywhere ecosystem or focusing on your endpoint environment. Narrowing the scope can significantly reduce operational load on your team while still allowing for measurable outcomes to benchmark future, broader rollouts.
For this example, we'll consider a program that focuses on an organization's endpoint infrastructure such as desktops, laptops, and mobile phones. By limiting the scope, your team can allocate resources effectively, refine processes, and address challenges in a controlled environment. Once proven methodologies and actionable results are established, the program can be scaled to cover broader areas of the security ecosystem.
Enabling an effective scoping exercise
Identifying the priority attack surface for your CTEM pilot is only the first question of an effective scope. Depending on your path forward, your team must fully understand the scope of assets and defensive controls in place.
During the scoping phase, your team should:
- Utilize any asset inventory tools to comprehensively compile and map the attack surface. In this case endpoint devices like workstations, mobile phones, servers, etc.
- Document existing, relevant security controls and their implementation such as the coverage and configuration of your EDR and endpoint management toolssome text
- Security control validation tools such as an ASCA platform can automate much of this process
- Prior to discovery, validate those security controls are fully operational, cover all assets, and are optimized to current recommended standards
From the scoping phase, your team will progress in the diagnosis of your existing attack surface by identifying any gaps and weaknesses in your now well-documented control environment.
Discover existing vulnerabilities and weaknesses
Now that you've scoped your existing attack surface and subsequent defensive controls, the next step is to uncover vulnerabilities, misconfigurations, and unprotected systems that attackers could exploit. The goal of the discovery phase is to identify potential attack paths and prioritize them based on their potential risk and impact.
By leveraging tools like vulnerability scanners, security control validation platforms, and attack surface mapping, organizations can compile a comprehensive list of their security gaps. This process should expand on the scoping phase to identify weaknesses within what has been outlined as the attack surface such as unpatched software, overly permissive access, or suboptimal configurations.
A well-executed discovery phase not only highlights the vulnerabilities within the environment but also sets the stage for effective prioritization and remediation efforts. For example, attack surface mapping provides a visual representation of how potential attackers could navigate your organization's defenses, while security testing offers deeper insights into how those pathways might be exploited or are currently being detected. The outcome of this phase is an actionable list of vulnerabilities and exposures that will inevitably be prioritized based on risk and business impact, ensuring resources are directed where they are needed most.
The biggest risks posed in this stage can often be the sheer volume of vulnerabilities. Where robust discovery stages incorporate various scanning, mapping, and testing exercises, the output can be overwhelming. Automating as much of this process through testing platforms and ensuring robust communication between teams can mitigate this, but it's imperative to understand that vulnerabilities will inevitably be triaged and addressed.
The key to an effective CTEM program is not just this groundwork, but its persistence, as future discovery phases should return fewer vulnerabilities when implemented effectively. This stands in contrast to traditional vulnerability management, which can often be an ongoing loop of the same vulnerabilities, as they are never effectively prioritized.
Prioritize based on risk and business impact
The key to effective threat exposure management lies in deciding which vulnerabilities to address first. Traditional vulnerability management programs or standalone testing programs live and die when teams receive laundry lists of red, with no context on how to address. Attempting to resolve all risks simultaneously is not even impractical—it's impossible. This stage is critical to a successful, ongoing program.
Quantifying and prioritizing risk can be a challenging, subjective undertaking, so it's important to incorporate a volume of feedback and factors when doing so. Leveraging insights from your work to date (scoping, testing, scanning, etc.) as well as qualitative feedback from your stakeholders and defensive teams, consider the following for each of the discovered vulnerabilities:
- Exploitability: How likely is it that the discovered vulnerability will be exploited?some text
- A vulnerability with no existing exploit available and requiring highly specialized knowledge of a particular platform to exploit should be considered less likely to occur compared to a vulnerability with publicly available exploit code and minimal technical barriers.
- Criticality: Does the asset hold sensitive data or power mission-critical systems?some text
- Vulnerabilities impacting your crown jewels, such as a database server containing customer financial information should be given a higher weight than say those impacting a marketing device used only at promotional events.
- Business Impact: How will a breach in the system affect operations, revenue, reputation, or compliance?some text
- An extension of criticality is impact beyond just loss of data. If the same customer database were exploited, the risk of regulatory fines and loss of revenue as a result of broken customer trust continues to add priority to a potential vulnerability.
During this stage, the Common Vulnerability Scoring System (CVSS) can be deployed, especially as a supplement to an internal framework built for your program. Part of building a successful CTEM program is understanding that your unique business case and scenario, which is essential context that traditional models and tools tend to ignore, leading to overextending resources on security efforts that aren't as impactful for your risk tolerance and needs.
Validate with real, continuous evaluation
Once high-priority risks are identified, your program should move into an action-oriented stage, evaluating existing controls against those potential threats. Up until this point, your enabling technology has potentially mapped techniques and threat intelligence against your control configuration to identify potential gaps. Now, you have to understand how those vulnerabilities and defenses would fare in a real-world attack.
Continuous threat exposure management requires that these vulnerabilities are identified and tested regularly in order to effectively respond and mitigate your risk. As drift occurs, your threat profile changes. The goal for this stage of your program to be able to answer the following:
- Can these vulnerabilities be easily exploited?
- How effective are my detection and response systems?
- What is the potential impact of exploitation?
At its core, this endeavor is served best by enabling red and purple team exercises, either through service engagements or autonomous tools. As we've mentioned previously, the goal is to start small and scale the program, as biting off more than a team can chew can quickly derail your efforts.
When prioritized effectively as they have been up until this point, red and purple team exercises can effectively answer the questions above. Where your red team focuses on exploitation and lateral movement or escalation, your purple team can validate the quality of detections and their efficacy to alert on these behaviors.
The goal of this stage is to develop a deep understanding of these priority vulnerabilities. Just as you prioritized those you wanted to validate and test, you must also prioritize the remediation. By answering the questions above during your CTEM program, you can equip your team with better insight into where to focus response efforts. Vulnerabilities with high business impact and risk scores that were ultimately very difficult to exploit might not be the focus of your immediate efforts until another development cycle.
Mobilize your teams to mitigate risk
Firmly in the action stage of your program, the final step in this development cycle is to mobilize your efforts to resolve some of these identified vulnerabilities. Perhaps the greatest value of a successful CTEM program is ruthless pragmatism. Where many security teams can get stuck in silos with disparate goals, the goal of CTEM is to align security teams with common strategic and technical priorities.
By first understanding the scope of the environment, its vulnerabilities, their potential risk, and how existing defenses measure up against those vulnerabilities, teams are better equipped with actionable insights when it comes time to remediate. In other circumstances where they skip the validation stage, they might waste hours on drafting a detection for a high-risk vulnerability that in truth, is low-risk due to a higher degree of difficulty.
With a reframed—and validated—understanding of how these vulnerabilities exist in their environment, teams can take the following steps to mobilize and mitigate:
- Define actionable goals: Clearly specify what needs to be fixed, such as pushing a new OS update to certain systems, reinstalling EDR, drafting a new detection, etc. These should be time-bound and complete before the next cycle.
- Collaborate across teams: Teams, including leadership, should be aligned on completing these goals with similar work to drive the chosen outcomes with fewer organizational hurdles. If a new detection is being written, the detection should be validated to ensure its efficacy.
- Track and evaluate outcomes: As CTEm is continuous, the updates to your defensive posture become part of your next scoping and discovery phase. In this way, your security posture is ever-improving and continuously validated for efficacy.
Building a resilient security framework with CTEM
Continuous threat exposure management (CTEM) programs can certainly have the curb appeal of more fodder for the alphabet soup of security. But in truth, it's a mindset. It shifts enterprise cybersecurity from reactive problem-solving to proactive risk mitigation.
Not only does this ideally alleviate operational load on increasingly overworked and burnt out teams, but enables those teams to elevate their security posture proactively. Where modern security controls often market around the "next thing" that can improve your security, a successful CTEM program maximizes those controls against relevant threats.