Follow the latest innovations on the Prelude platform
.png)
Map control configurations against the latest threats
In addition to regular monitoring of security control coverage and configuration, Prelude users can now map those configurations against the latest threats to better understand their protection against relevant threats. Users can visualize gaps in their control configuration based on missing or suboptimal policies and controls against th relevant MITRE techniques in a given threat.
This enables users to quickly operationalize their threat intelligence and view a technique-by-technique breakdown of their controls, along with deep-links to specific controls to quickly fill any gaps.
.png)
Security control monitoring and configuration
Prelude has released foundational capabilities for capturing the latest insights from a wide range of security controls, including their deployment, configuration, and efficacy. Continuous monitoring, powered by read-only APIs affords for constant visibility into the state of your defensive controls and whether they are performing as expected.
This release includes foundational capabilities for the below, among others:
- Asset or endpoint management to determine breadth of the estate
- Endpoint detection and response (EDR) to determine the coverage of the control
- Policy configuration and deep links to integrations for rapid remediation
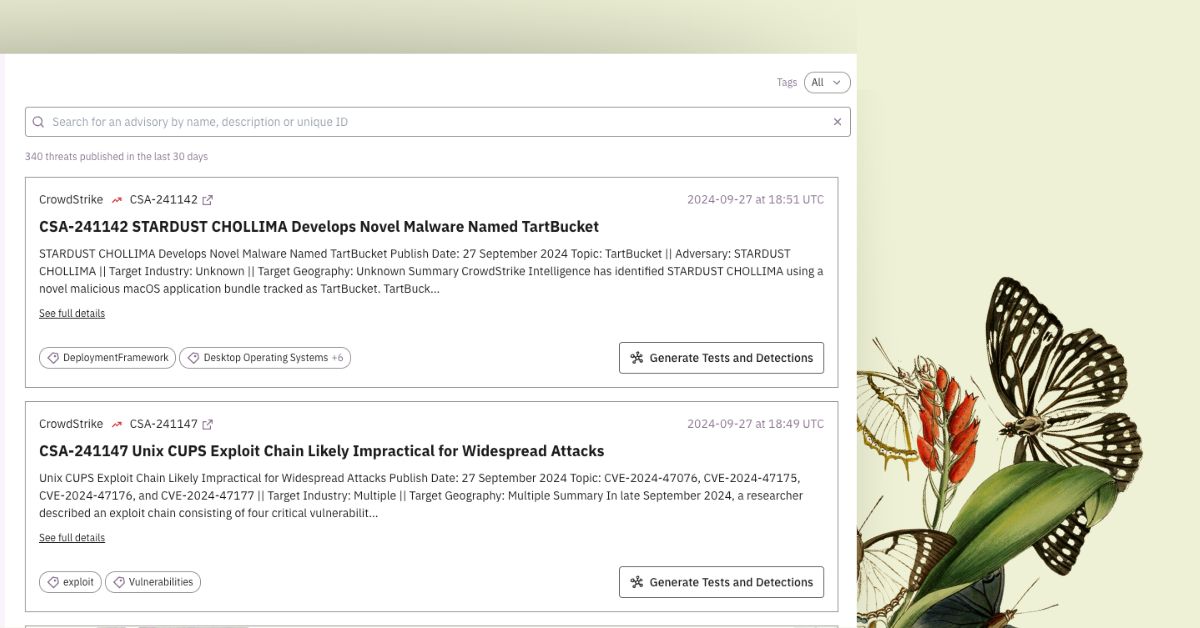
Automatically transform CrowdStrike threat intel
CrowdStrike customers can now leverage Prelude's automated threat intelligence assistant alongside a feed of CrowdStrike Threat Intelligence. With one click, users can generate bespoke tests, threat hunt queries, and detection rules designed to evaluate and augment defenses against the behaviors referenced in that intelligence.
Along with the release of threat intel feed integration, Detect users may now:
- Edit expected outcomes on a per test basis based on organizational needs
- Leverage Prelude's AI to create, edit, and regenerate custom tests in their own environments
- Configure SSO via OIDC
.jpeg)
Observe, Detect, and Prevent
Detect now offers comprehensive reporting on the observed, detected, and prevented information for Prelude tests in CrowdStrike. Tests in platform now include an expected outcome (Observed, Detected, or Prevented) to provide holistic visibility into your security posture. Enhanced dashboards and details views display these new metrics alongside expected outcomes to provide deep insight into tests results and where failures are occurring in your defenses.
In addition to the release of deeper ODP insights, Detect users may now:
- Schedule up to 500 threats and tests, an increase from 250
- Customize and include additional columns in the Insights Dashboard, along with additions of dashboard tables for Threats, Tests, and Endpoints
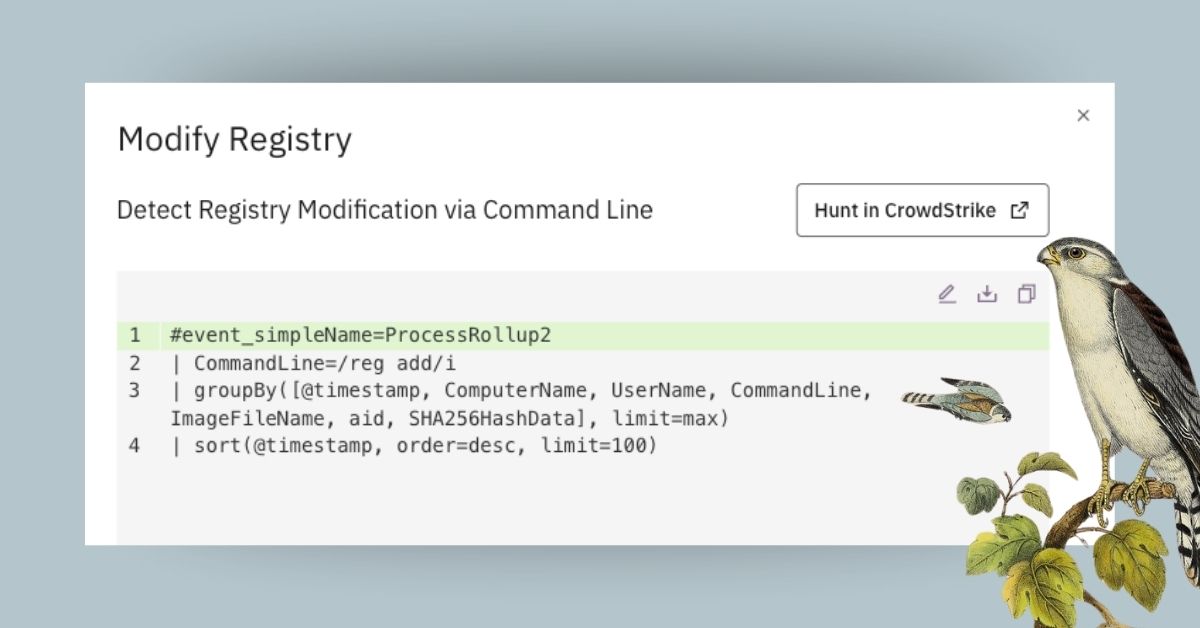
Automatically generate and initiate threat hunts
Following the release of our Automated Threat Intelligence Assistant in May, Detect users can now expect to generate relevant hunt queries for threats uploaded to the platform. Hunt queries are generated alongside security tests and detection rules, affording users the ability to quickly evaluate whether there is evidence of techniques associated with the threat in their systems to date.
Along with the release of threat hunting queries, Detect users may:
- Regenerate or conduct inline edits to any generated tests, detections, and queries prior to importing to Detect. Edits can also be made via the threat's detail view
- For CrowdStrike users, hunt queries are deep-linked to the FalCon Insight platform, enabling users the ability to initiate one-click threat hunts
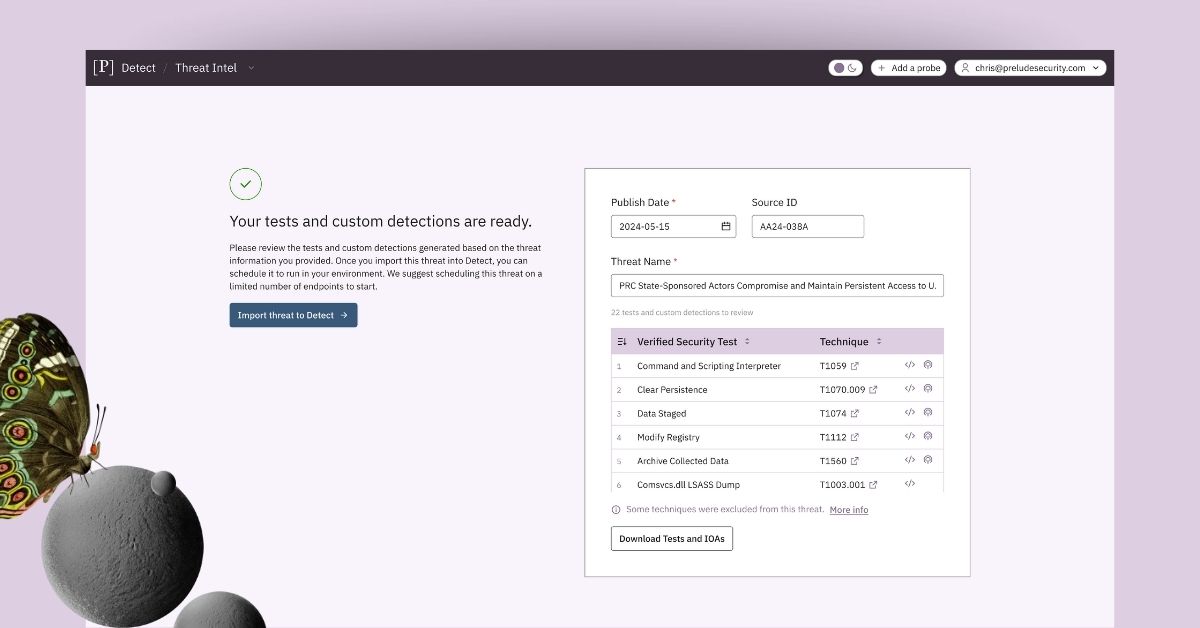
Automatically transform threat intelligence into validated protections
Detect users can now upload PDFs of available threat intelligence into our Automated Threat Intelligence Assistant to rapidly generate relevant security tests and custom detection rules to import into and deploy via the Detect platform. This enables users to quickly evaluate defenses against new threats, while providing an EDR-ready detection to instruct your defenses to alert on or prevent these behaviors in the future.
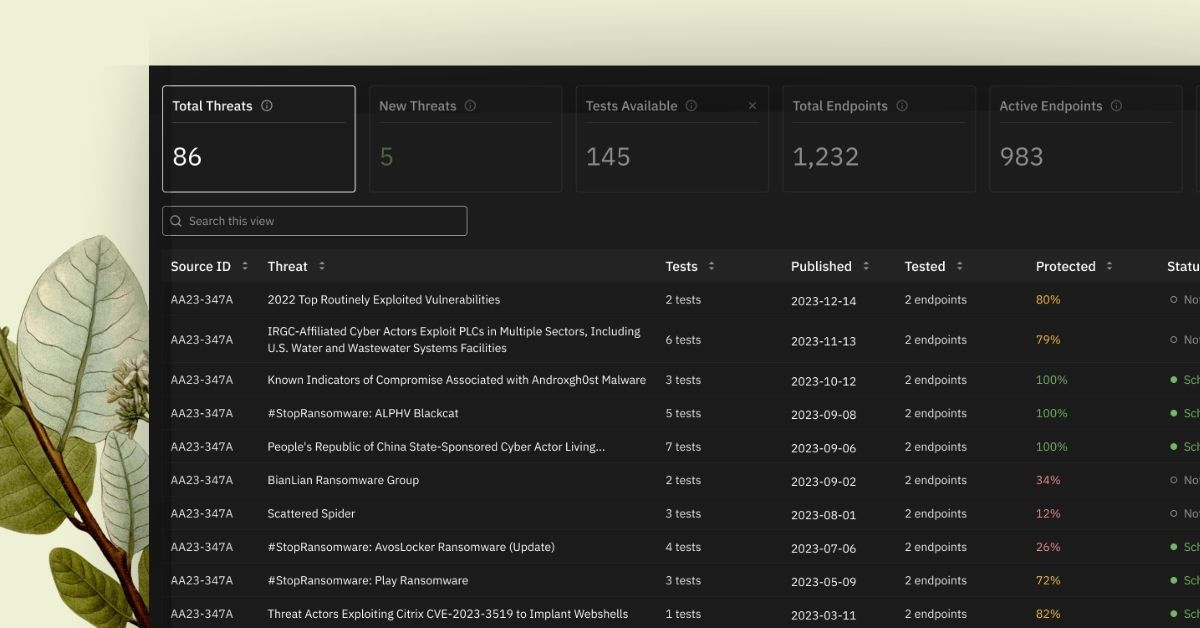
Reformatting Verified Security Tests
Prelude has released a refactoring of how tests are presented in deployed in Detect, now known as Threats. Tests are nowbroken out by MITRE ATT&CK TCode, with each TCode having its own test. This affords Detect users to evaluate defenses against all TCodes associated with a given Threat.
In addition to test refactoring, Detect users may now:
- Schedule Threats to be evaluated against targeted endpoints, with each test in the Threat running
- Explore each associated test in the new Threat detail view
- Schedule Threats or Tests to "Run Once" in addition to existing recurring schedule options
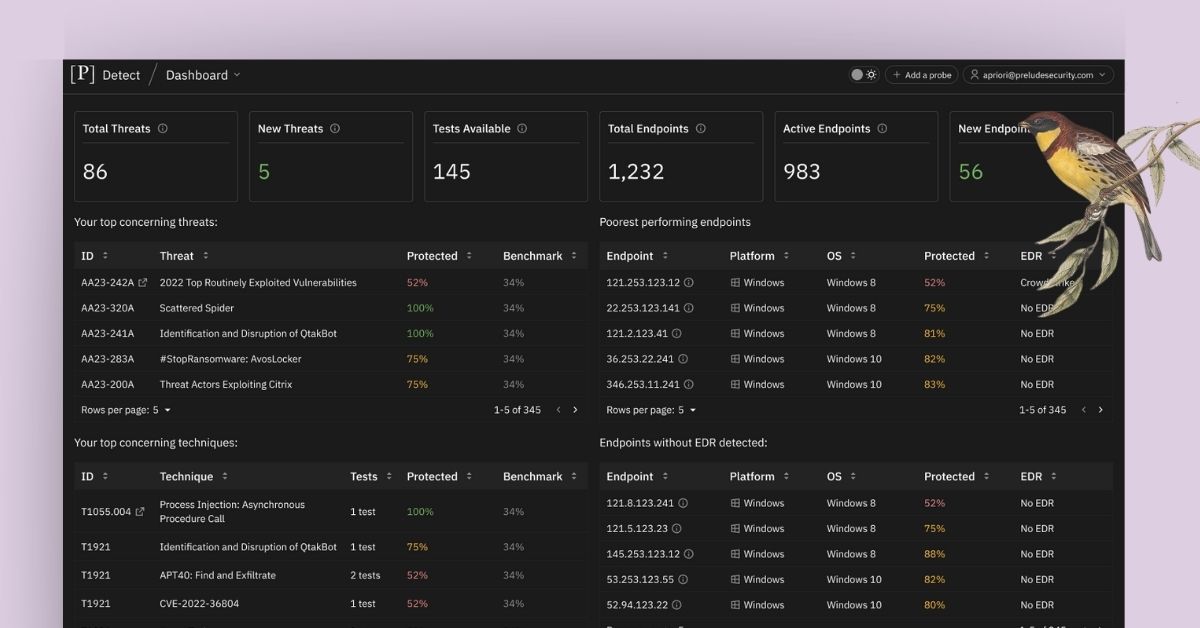
Deeper insight into Detect activity
When logging into Detect, users are now taken to the new Dashboard page. Detect's new Dashboard shows a historical view of your hosts' protection, with details about top advisories, and endpoints. This coincides with the release of our new Activity Dashboard, providing a detailed list of endpoints filterable by Test, Platform, Operating System, EDR, and EDR Prevention Policy and their protection levels with accompanying recommendations for possible protection level increase.
Along with the release of updated dashboards, Detect users may now:
- Access the platform via Single Sign On, with configurable OIDC authentication through Microsoft, Google, or Okta
- Power advanced alert suppression associated with our CrowdStrike and Microsoft Defender integrations

Experience every update first hand
Quickly discover the gaps in your tools with a 14-day free trial of Prelude and optimize the tools you already own in minutes, not months.
