Better Security Starts With Aggregating Your Asset Inventory
For many organizations, managing IT assets is like trying to complete a jigsaw puzzle without all the pieces. Despite massive investments in security tools and controls, many companies still have critical gaps in their ecosystems that leave them vulnerable to breaches.
Often, these gaps stem not from a lack of tools—if such a thing exists in security—but from incomplete visibility and integration across those tools. By aggregating and analyzing data from multiple systems, security leaders can gain a more robust picture of their IT inventory and subsequently, their security posture.
The challenge with disparate security tools
It’s not unusual for enterprises to deploy a wide array of security tools. The average organization uses roughly 10 security tools, covering everything from endpoint management to identity and access control. These tools, however, often operate in silos, creating fragmented and occasionally contradictory reports.
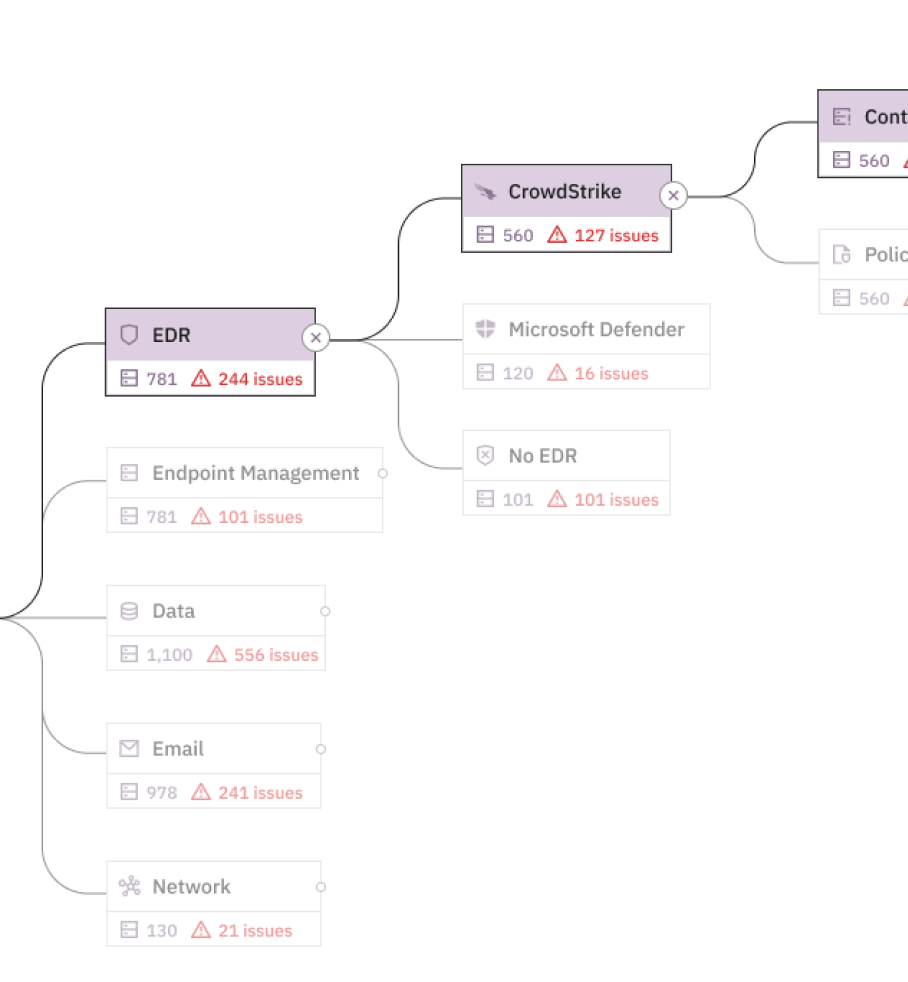
Let's look at a practical example. Consider an organization using these tools:
- Microsoft Intune and Jamf for mobile device management (MDM)
- CrowdStrike for endpoint detection and response (EDR)
- Tenable for managing vulnerabilities
- Microsoft Entra for identity and access management (IAM)
On paper, each system might appear to report accurate asset figures—for example, both Intune and Jamf might show 5,000 managed devices, while Entra reports 4,500 user accounts. At first glance, everything looks secure. But when the inventory from these tools is collected and analyzed in the aggregate, a much more complex picture emerges.
Finding the gaps in disconnected data
The first step in finding any gaps in your control inventory is typically a lengthy, manual effort. Perhaps data is exported and dumped into a complex, multi-tab nightmare spreadsheet. Others may turn to more nuanced but equally challenging SQL and Power BI queries. Aggregating asset and control inventory has been one of the foundational capabilities we're building at Prelude to reduce dependency on lengthy, manual exercises that ultimately contribute enormous value to your security program.
Whatever the path to correlating which devices have X and Y tools, surprising discrepancies often come to light. Leaning on our previous example, we may find now that our actual inventory is 5,500 managed endpoint devices, not 5,000. And within this aggregated data set:
- 200 devices are missing CrowdStrike's sensor protection.
- 300 devices lack MDM coverage, leaving them without configuration policies.
- 100 devices are missing Tenable data, meaning vulnerabilities aren’t being tracked.
Even more concerning would be any issues related to the functionality and efficacy of existing security tools on those new devices:
- 150 devices (3%) have a broken or misconfigured EDR system, meaning they’re operating in a suboptimal state, like CrowdStrike's Reduced Functionality Mode.
- 300 devices (6%) lack recent vulnerability assessments.
- 200 devices (3.5%) that should report to MDM haven’t done so recently, making them effectively rogue devices.
When we apply the same process to our users, the gaps can be just as alarming:
- Of the 4,500 users in the directory, 75 users have no associated device record in critical security controls, making their devices completely unmanaged and unknown.
- Of the 75 users, 15 are high-risk users with access to sensitive data (like your finance and sales teams), compounding the threat to organizational security.
Because these disparate security tools don't talk to one another, these gaps are rarely visible when each tool is evaluated in isolation. Looking at asset management in the aggregate, however, detects them, offering organizations a previously unattainable level of insight into their true security posture.
How does any of this happen?
One of the biggest challenges in cybersecurity is not new threats and vulnerabilities, but an unclear picture of what needs to be secured. When I ran product management at Tanium, we often found that between 10-15% of an organization's devices were unmanaged and missing at least one management or security tool. While this happens quite easily already, remote work and an increasing number of tools available means the likelihood for gaps to pile up has only grown.
As a security leader, you may inherit that company with 4,500 employees and 5,000 devices. These are the known variables. You have contracts for CrowdStrike for 5,000 devices, Entra for 4,500 users. So on, and so forth.
But perhaps other devices were never properly retired or acquired through non-standard channels, such as bring-your-own policies or temporary project teams. Small oversights like these pile up. Devices get added without proper tracking, and as the business grows and evolves, the gap between what you think you have and what you have widens. With inventory happening on many different platforms, the things you don't know can hurt you.
How an aggregate asset inventory supports your security program
Control gaps, missing data, and misconfigurations aren’t just technical hiccups; they can be the difference between thwarting a cyberattack and suffering a career-ending breach. Many security teams and tools get hung up on false positive suppression, tuning detections, and the next best vendor. But knowing what to secure—and ensuring your current tools are doing so—is a lion's share of the battle.
Complete visibility into what you need to secure
Looking at asset management in the aggregate provides a single source of truth for IT inventory by consolidating data from all your various security tools. Instead of relying on each tool’s reports, organizations gain a unified view of their assets, including devices, user accounts, and cloud resources.
Not only does this expose any blind spots in your control environment, but it affords greater operational efficiency for your team. With a single source for your inventory, your team spends less time reconciling disparate reports and more time focusing on meaningful improvements to your program.
Improved control coverage and performance
The simplest way for an attacker to evade EDR is to go where it isn't. By aggregating data, organizations can ensure that critical controls—such as EDR, MDM, and vulnerability management—are applied consistently across all assets. It’s much easier to identify which devices are missing protections or misconfigured when you’re looking at the full picture.
Aggregate asset management highlights gaps in real-time, allowing teams to address vulnerabilities before attackers exploit them. Whether it’s a rogue device, a misconfigured control, or outdated vulnerability data, these risks can be mitigated proactively when they’re visible.
Justification of control investments
Best-of-breed security tools are only as effective as you enable them to be. You invest heavily into tools like your EDR and IAM platform and have certain expectations of what they'll do to protect your business. Those tools immediately lose value when entire segments of your estate aren't being covered or have fallen into suboptimal performance states. By establishing your full inventory of assets, you can lay the foundation for a better defense built with tools you're already invested in.
Better security starts with a better inventory
The complexity of today’s IT environments demands a new approach. Aggregate asset management ensures the most comprehensive visibility into your assets, strengthens security tool integration, and delivers actionable insights to close critical gaps in your security posture.
If you'd like to learn more about what we're doing at Prelude to make this an easier reality for teams at scale, create an account and start connecting your tools.
Start monitoring controls free for 14 days