For many security teams, operationalizing threat intelligence is like trying to read a map with the legend missing. MITRE ATT&CK has become the go-to framework for understanding attacker behavior, but knowing which techniques apply to your environment and how to defend against them using your existing tools. That’s still a massive challenge.
The issue isn’t a lack of threat intel. Most organizations today have access to rich intelligence feeds and regular reports outlining emerging threats—often complete with MITRE technique references. The real problem is translating that knowledge into action across a complex stack of endpoint protection tools, configurations, and detection rules.
The disconnect between threat intel and control configuration
Let’s walk through a common scenario. You’ve received a threat report highlighting techniques like T1055.001 (Process Injection) and T1562.001 (Disable or Modify Tools). The report looks thorough and urgent. But what do you do with it?
If you’re like most teams, the answer involves digging through EDR and AV dashboards, trying to decipher if your tools can actually detect or prevent those techniques—and if the settings are correctly configured to do so.
For instance:
- Does your EDR tool have coverage for T1055.001?
- Is the behavior detection engine even turned on?
- Are exclusion lists accidentally creating blind spots?
- Has a misconfigured policy neutered a critical detection?
And maybe most importantly—how would you even know?
Manual mapping is a nightmare
Mapping MITRE techniques to your security stack manually is slow, error-prone, and often out of date the moment it’s completed. Some teams attempt to track this in sprawling spreadsheets, others through wiki pages or ticket systems. But keeping up with the evolving threat landscape while maintaining confidence in your tooling configuration is a full-time job (and then some).
Even assuming you can map a technique to a setting or policy, figuring out whether it’s optimally configured adds another layer of complexity. What’s the recommended setting? Is your agent even functioning properly on all endpoints? Is anyone monitoring drift?
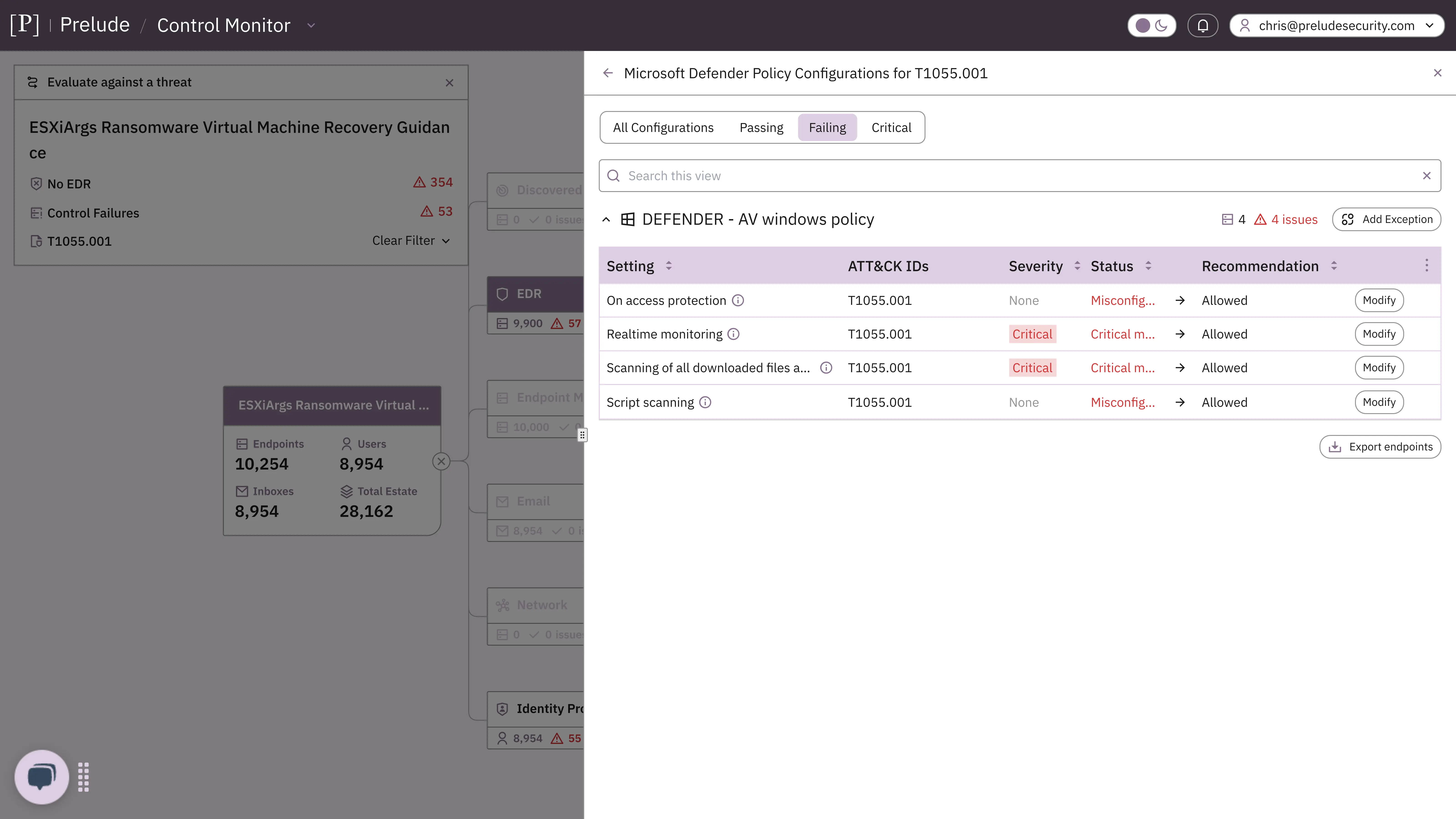
Turning threat intel into actionable insight—instantly
That’s where Prelude comes in.
With one click, we overlay the latest threat intelligence—complete with MITRE mappings—directly onto your existing controls. Our platform:
- Maps each MITRE technique to your specific AV/EDR features and settings
- Identifies whether those controls are present and active in your environment
- Assess if they’re optimally configured to defend against the identified technique
- Shows exactly what needs to be changed (and why)
- Provides a direct link to jump into the relevant console or policy to make the change
In short, we bridge the gap between “this is what the threat does” and “here’s how to make sure we’re protected.”
Misconfigurations and agent issues? You’ll know—immediately
But even the best configuration is only as good as its runtime state. That’s why we go a step further. Our platform continuously monitors the status of your integrated security tools—AV, EDR, and more—and offers real-time alerting via Slack or email when:
- An endpoint agent is in reduced functionality or error mode
- A policy fails to apply or drifts from the baseline
- A misconfiguration weakens your coverage against a known technique
- A protection feature is disabled, missing, or excluded
This means your security team gets notified as it happens, not weeks later during a periodic audit.
Why this matters for your security program
Security isn’t just about coverage—it’s about effective coverage. Frameworks like MITRE ATT&CK have pushed the industry forward by providing a common language for adversary behavior. But unless you can clearly see how your tools map to that behavior, you’re flying blind.
Let’s be honest: most AV and EDR products have hundreds of settings. Some of those settings are critical for stopping specific attack techniques, but figuring that out manually is exhausting. And assuming those settings stay correctly configured is wishful thinking without proper validation and monitoring.
Operationalizing MITRE, without the pain
By automating the mapping between MITRE techniques and your existing controls, and validating their state continuously, our solution gives you:
- Immediate clarity into your defensive posture
- Confidence that you’re covered against emerging threats
- The ability to respond fast when gaps are found
- Evidence to justify and optimize your existing security investments
You already have strong tools in place—now it’s time to make them work smarter. With our platform, you can move from “I hope we’re covered” to “I know we’re covered”—and if we’re not, I know exactly what to fix.
Maximize your security tools while minimizing your effort