What To Do During Your Free Trial of Prelude's Control Monitoring Platform
Your security tools are only as effective as how they're deployed. It can be all-too-easy to fall into a mindset of set it and forget it when it comes to the tools we expect to protect us on a regular basis. But maintaining a robust security posture means staying on top of the deployment, health, and configuration of those tools, especially with how heavily we invest in them.
With a free trial of Prelude's continuous monitoring platform, teams can capture a high-level view of how their security tools are performing today, and monitor for drift over time. Here are three practical ways you can make the most of your trial.
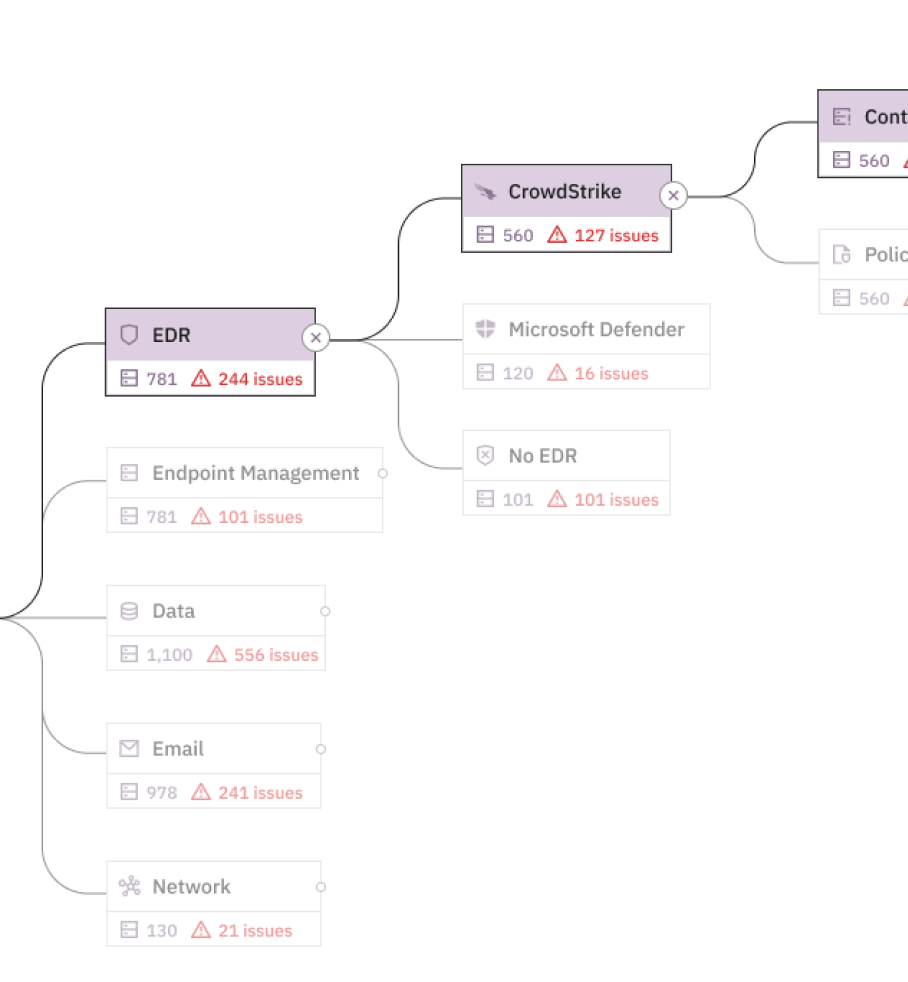
1. Find devices and users missing critical controls
Enabling multifactor authentication (MFA) and deploying an endpoint detection and response (EDR) tool are two of the most foundational things you can do to shore up defenses. While it might not be as flashy as the countless hours invested into tuning your a new detection logic, that logic is largely moot if any device is missing EDR. The best way for an attacker to evade EDR—is to go where it isn't.
By ingesting data from your asset management platform and your EDR tools via read-only integrations, Prelude quickly correlates which devices in your estate are lacking the EDR's agent. From there, you can triage which devices need immediate attention, and set up notifications should any devices fall into this state as your environment is continuously monitored.
Even with EDR installed, threat actors often capitalize on stolen or weak credentials. By requiring users to leverage an authenticator app, biometric identifier, or a passcode—MFA reduces the risk of unauthorized access, even if a password is compromised. By connecting your identity management platform to Prelude, you can quickly identify users missing MFA, along with any users failing to adhere to your organization's password policies.
2. Evaluate policies for weaknesses and monitor drift
Every security tool has their own unique deployment and configuration based on your environment and their own recommended best practices. Understanding how your policies are configured against those best practices gives your team better insight into how to optimally configure your tools and maximize the investments you already have.
Further, drift can occur due to software updates, multiparty deployments, or human error, leaving your environment open to threats in scenarios where your team would never be the wiser. Continuous monitoring keeps your team on top of drift, enabling teams to fill gaps as they occur.
In the case of one financial firm leveraging Prelude, the team was notified of a large number of production endpoints continuously falling into a suboptimal prevention policy in CrowdStrike. Specifically, "Vulnerable Driver Protection" was disabled, making these systems vulnerable to bring-your-own-vulnerable-driver (BYOVD) attacks. This type of attack allows threat actors to exploit outdated or poorly coded drivers to deploy malicious software.
The misconfiguration stemmed from an incorrect hostname filter in a dynamic group assignment. Within minutes, the organization’s team identified the issue, updated the policy, and removed the dynamic assignment—eliminating the vulnerability.
3. Validate configuration against relevant threats
Understanding how your environment measures up to active threats is essential for staying ahead of attackers. Prelude allows you to evaluate your current configurations against specific threat intelligence, mapping controls and policies to MITRE ATT&CK techniques and identifying areas for improvement.
An investment firm recently underwent an exercise to validate controls against BlackBasta ransomware. During the process, Prelude flagged a misconfiguration within their EDR. Specifically, "Sensor Machine Learning" was in its default setting, leaving the system vulnerable to three of the six techniques identified. After identifying the gap, the team was able to leverage Prelude's in-app recommendation and deep-links to their EDR to quickly enhance the setting and optimize the detection capabilities within their EDR.
As the team continued on to more in-depth testing exercises, they were fully equipped to validate defenses with the knowledge their controls were fully deployed and optimally configured, focusing efforts on additional detection logic.
Getting started with Prelude
Prelude's continuous control monitoring capabilities enable teams to quickly survey their disparate security tools to identify gaps and policy misconfigurations to put those controls in fighting shape. While ongoing monitoring and robust alerting keeps teams ahead of the drift that's commonplace in dynamic IT environments.
During your trial, you can quickly:
- Surface missing controls like MFA and EDR to close high-risk gaps
- Optimize and monitor security policies to reduce drift and ensure optimal deployment
- Validate configurations against the relevant threat intelligence to prioritize tactical efforts
Start monitoring controls free for 14 days