Insights from the SANS Detection and Response Survey
We recently sponsored the SANS 2024 Detection and Response Survey—surveying 400 respondents about the technology, resources, and processes teams are using to build and measure their detection and response capabilities, and what's holding them back.
Inevitably, resourcing looms large as we move into 2025, with budget and teams cited as a frequent challenge for teams in their efforts. The full report is available here, but we break down some of the insights below, alongside our recommendation for organizations to get the most out of their existing resources.
EDR tools are essential, but complexity remains
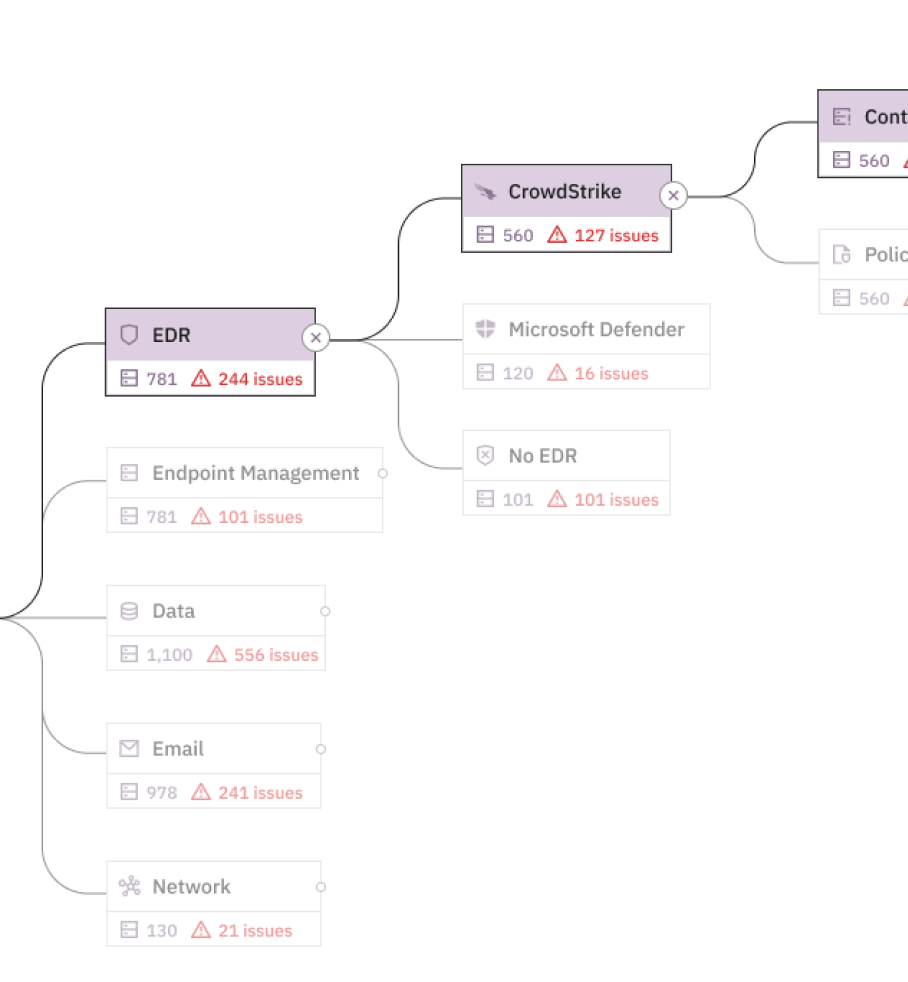
According to the survey, 82% of respondents identified endpoint detection and response (EDR) as one of their most valuable tools. Perhaps something of a self-fulfilling prophecy, as an organization's EDR is relied on for both threat detection and powering incident response.
At Prelude, we've always been advocates for understanding your EDR. Because, despite its declared criticality, data breaches continue to start at the endpoint—including 70% of those evaluated in IBM's Cost of a Data Breach report in 2024. This report underscores the importance of the EDR, yet it is still an incredibly complex tool—requiring vast technical knowledge to deploy and tune effectively.
Innumerable settings powered by opaque detection logic make it difficult for teams to fully understand how the tool functions, leaving critical gaps in both configuration and deployment. Where smaller organizations might hope to set and forget, tools like an EDR are only as effective as the people operating them.
All of this builds to another key takeaway from the report:
Bridging the skill gap in security operations
The work needed to effectively manage defensive tools, draft detections, and tune the logic typically requires highly-technical individuals with tailored skill sets. The survey revealed that 59% of organizations struggle to maintain adequate detection capabilities due to a lack of skilled personnel.
Many organizations (61%) supplement their teams with consultants and service agencies This dependence on outside help highlights a growing concern for hiring and retaining qualified staff. Regulatory requirements and the risk of a breach means security talent will always remain in-demand, but consolidation efforts and leaner organizations can often expect too much from too few individuals.
Not to mention, the work is still complex. The amount of deep technical expertise into tooling, adversary tradecraft, and detection logic throws up multiple roadblocks on new hires. It also means those individuals that achieve that level of expertise are vital to keep around.
All of this bubbles up to overburdened or leaner teams facing the same volume of challenges leveraging complex systems like EDR while continuing to maintain day-to-day operations. If members of a SOC don’t fully understand the detection tool or its logic, activities like purple teaming and detection validation become increasingly difficult to execute.
Though 77% of respondents are prioritizing broad strokes training and skill development, the level of expertise required means tooling should more readily accommodate the team. Being able to easily understand your EDR and other defensive tools' configuration drift, deployment, and health is another part of validating that detection systems and logic are actually protecting against the attacks we expect them to. This should be easier, but plenty of teams continue to face these challenges.
Extracting more ROI from limited security budgets
Only 26% of surveyed organizations believe their budgets are sufficient for their security efforts, and a mere 5% describe them as more than sufficient. With tight budgets, security organizations must carefully prioritize investments to ensure that limited resources have maximum impact.
This only fuels the challenge of hiring—and retaining—skilled security practitioners when their skills are in high demand and budgets are thin. Security controls (like an EDR) and headcount are among the most significant investments for many organizations—but without regular evaluation and optimization, they can fail to deliver their full potential.
A lack of funding forces teams to operate lean, leaving little room for error. Ill-configured tools or underperforming controls can be a costly oversight when budgets are stretched thin. With many security operations and detection teams focused on incident response and detection engineering, control monitoring and efficacy can often fall by the wayside.
The reality is, without that foundational work in place, testing, validation, and response work can falter. How can you validate the efficacy of a detection when your EDR is not fully deployed? Get the full value of identity management when some users roll without MFA?
Your teams are better equipped—and budget better spent—when your tools are regularly monitored and optimized for misconfigurations and suboptimal performance.
Making the most of your security controls
From insufficient budgets to tool complexity and talent shortages, the 2024 SANS Detection and Response Survey underscores the very real challenges facing cybersecurity teams. However, it also highlights key areas where organizations can act strategically to amplify their defenses.
At the core of achieving operational excellence in detection and response is understanding whether your tools and systems are working as expected. That’s where you can take the first step toward optimization. Prelude provides the critical monitoring and validation that your controls are working as expected—equipping teams with actionable insights in lieu of additional noise.
Start monitoring controls free for 14 days